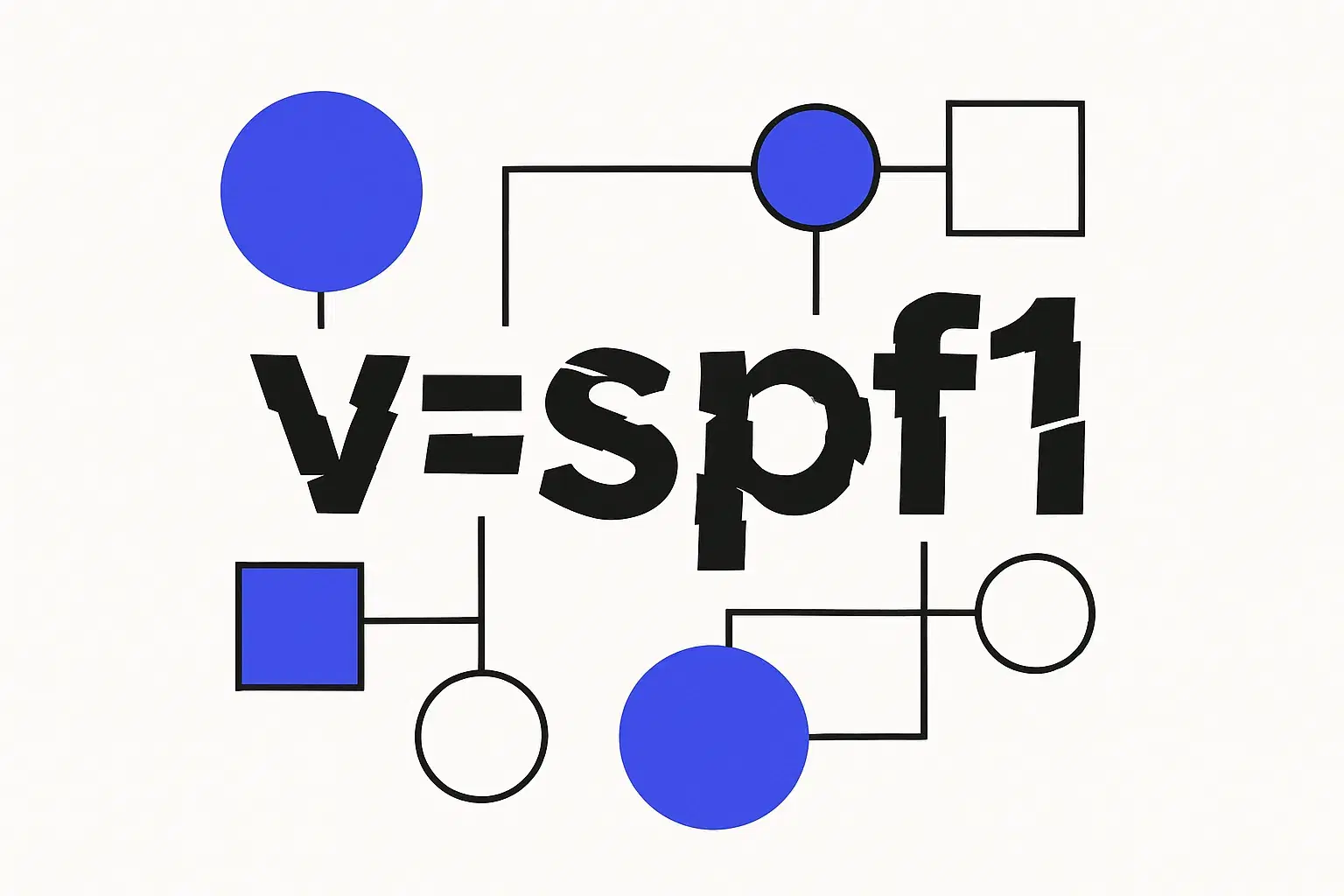
Understanding v=spf1: The Foundation of the Sender Policy Framework
In the field of email authentication, v=spf1 forms the backbone of the Sender Policy Framework (SPF). SPF is an authentication protocol that specifies which mail servers have the authority to send emails on behalf of your domain. Using the correct v=spf1 record, often referred to simply as an SPF record, improves email legitimacy and combats spoofing attempts.
Whether you manage email for a small business or an enterprise, understanding how SPF and v=spf1 function is vital to avoid deliverability problems. From setup to troubleshooting, a strong grasp of these records will strengthen your domain’s trustworthiness with major mail providers like Google and Microsoft. In this guide, we’ll thoroughly explore v=spf1, examine different email platform requirements, and provide actionable steps for managing SPF across multiple domains.
How SPF Works: Unpacking the v=spf1 Mechanism
The Sender Policy Framework operates by letting domain owners publish authorized sending sources in Domain Name System (DNS) records. The line always starts with v=spf1. When an email server receives a message, it checks the sender’s domain for an SPF record. If the sending IP matches entries in the SPF policy, the server accepts the message; if not, the message could be flagged or rejected.
- v=spf1: Indicates the version of SPF being used.
- ip4/ip6: Lists authorized IPv4 and IPv6 addresses respectively.
- include: Refers to other domains’ SPF policies for delegated authorization.
- all: Defines a default action for emails not matching previous rules.
A properly configured v=spf1 record guards your domain against spoofing and unauthorized use, thereby improving acceptance rates across mailbox providers.
For example, a basic SPF record may look like this:
v=spf1 ip4:192.0.2.0/24 include:thirdparty.com -all
In this setup, emails originating from 192.0.2.0/24 or systems allowed by thirdparty.com pass SPF. All other sources fail.
SPF for Google: Gmail’s Requirements and Best Practices
To ensure emails sent from your domain reach Gmail inboxes, Google checks the SPF configuration for accuracy. Their recommended SPF policy often looks like:
v=spf1 include:_spf.google.com ~all
Here, include:_spf.google.com allows Google’s own servers to send emails on your behalf. The ~all mechanism means “softfail,” which means messages from non-listed sources may still be accepted but marked as suspicious.
- Publish your
v=spf1in the DNS TXT record for the sending domain. - Use only approved mail senders; avoid listing broad ranges or public relays.
- Monitor changes, as Google occasionally updates its sending infrastructure.
Misconfigurations can send legitimate emails to spam. If you’re experiencing issues, revisit your SPF syntax and check for extra spaces, excessive mechanisms (under 10 DNS lookups recommended), or conflicting entries. Many organizations also find it helpful to align their SPF with other authentication protocols, but SPF remains the first checkpoint.
Microsoft’s Approach: SPF for Outlook and Exchange Online
Microsoft 365 (formerly Office 365) and Outlook.com use SPF in evaluating inbound mail. The primary difference from Google’s approach lies in the include mechanism:
v=spf1 include:spf.protection.outlook.com -all
-all signals a strict “fail” policy. Only senders matched in the SPF criteria pass. To ensure compliance with Microsoft’s threat filters, which may reject or quarantine emails failing the SPF check, consider the following steps for Microsoft domains:
- Add
include:spf.protection.outlook.comfor Microsoft 365 tenants. - Test with Microsoft’s Remote Connectivity Analyzer to verify your DNS.
- Regularly review organization settings, especially when adding new senders.
Multiple email sending systems (for example, when using a CRM and Microsoft 365 together) require merging SPF mechanisms using the “include” directive. A proper merge avoids conflicting records.
Dealing with Multi-Domain SPF Complexities
Operating with numerous domains and subdomains is common for many businesses today, complicating v=spf1 management. Each domain used for outbound email needs its own SPF record. Merging multiple sending sources or third-party vendors runs the risk of exceeding the 10 DNS lookup limit, a common reason for SPF failures.
Best Practices for Multi-Domain SPF Management
- Create unique SPF records per domain or subdomain instead of a “catch-all.”
- Lower DNS lookups by consolidating vendors and limiting unnecessary
includemechanisms. - Combine internal and third-party senders in a single record but stay under technical limits.
- Set up monitoring for each domain; use testing tools to verify actual email paths and checkups after changes.
When you reach the DNS lookup threshold, either review vendor recommendations or use SPF flattening services, which replace include chains with plain IPs. These strategies help ensure emails from every domain pass SPF checks without failure.
SPF Syntax: Common Pitfalls and Recommendations
Writing SPF records using v=spf1 syntax requires attention to detail, as nuances often trip up even experienced admins. Some of the frequent errors include:
- Forgetting to finish the record with an “all” mechanism, creating ambiguous results.
- Using unsupported or legacy SPF mechanisms.
- Mistakenly including duplicate mechanisms or contradictory entries.
- Exceeding the DNS lookup limits with too many includes or redirects.
Always validate your SPF record using external tools before publishing. Documentation from each email provider (such as Google and Microsoft) offers guidance specific to their platforms. Align these with your operational needs to prevent routine and hard-to-trace problems with deliverability and anti-spam systems.
SPF and Deliverability: A Real-World Perspective
The state of your SPF record can strongly influence whether your emails land in inboxes or are diverted to the spam folder. SPF failures occur more often than many realize, usually because of simple missteps like adding an extra space or omitting a sending service. Overly permissive policies open the door for spoofers, while overly restrictive ones cause legitimate messages to be rejected.
For an in-depth look at sender reputation and avoiding the spam folder, explore this detailed resource on improving your email sender reputation. It addresses interconnected factors, such as domain reputation, authentication, and feedback loops, that reinforce the work SPF performs.
SPF Strategies for Cold Outreach
Sales and outreach teams rely on cold email, making SPF an operational necessity. The moment a mailbox starts sending outbound email after a period of inactivity, recipients’ spam filters scrutinize each technical setting. A correct v=spf1 record reassures providers that messages are authentic, not junk.
- Use your SPF to list each outbound sending IP/system you control for outreach.
- Avoid “+all”; this opens the door to abuse. The default should be “~all” (softfail) or “-all” (fail).
- Periodically re-audit all vendors listed, especially third-party mailers.
Email warm up tools can be used in tandem with proper SPF to ensure new or freshly reactivated mailboxes build favorable histories with mailbox providers. As your outreach campaign matures, revisit SPF records at every major change, such as CRM adoption or expanded sending volume.
To further refine your outreach and deliverability, master email warm-up strategies for 2026 and see how technical foundations like SPF play a role in long-term inbox placement.
SPF Limitations and Complementary Protocols
While SPF with v=spf1 is valuable, it’s not bulletproof. Some limitations include:
- If an email is forwarded, SPF may fail because the forwarding server is not in the original record.
- SPF only checks the envelope “from” domain, not the visible “From” address, which can be manipulated.
- It cannot encrypt messages or reject at the content level.
Combine SPF with DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance) for a layered defense. These protocols work together to:
- Authenticate both the sending server and the message’s content.
- Define how unauthenticated emails should be handled (quarantine, reject, report).
Enforcing a DMARC policy on top of strong SPF and DKIM records gives complete coverage, helping your emails gain the trust of ISPs and recipients alike.
Maintaining and Auditing SPF: Ongoing Care for Seamless Delivery
v=spf1 records require regular attention. Changes to your domain, new vendors, or modifications to existing senders mean you should update SPF right away. Keep a calendar reminder to review your DNS every quarter. Automate SPF record checks with third-party auditing tools or scripts, especially if you manage several domains.
Pro Tips for Ongoing SPF Success
- Document every record change, including who updated it and why.
- Use version control or changelogs for your DNS/IT documentation.
- Deploy DMARC reports to catch forged sending attempts quickly.
- Test on non-production domains before rolling out widespread changes.
If you notice an uptick in rejections, errors, or unexpected spam placement, revisit SPF settings and check for vendor updates. When in doubt, consult your mail platform’s documentation or support, and review online SPF checkers for inconsistencies.
Conclusion: SPF Success Requires More than Just Syntax
Mastering v=spf1 and domain-specific SPF records strengthens your email security, improving deliverability and reducing the risk of spoofing. Whether configuring for Google, Microsoft, or operating multiple domains, attention to SPF details pays dividends with reliable delivery and reduced spam complaints.
By keeping SPF records accurate, monitoring changes, and aligning with contemporary email warm-up techniques to establish sender reputation, your inbox placement and sender reputation will remain healthy even as standards evolve. For insights on further troubleshooting and advanced strategies, keep up with industry documentation and routinely review your own practices.
Want some assitance for your email deliverability ? Hire an email deliverability expert!
FAQ
What is v=spf1 in an SPF record?
v=spf1 is the SPF record version identifier that indicates you are using the Sender Policy Framework to specify authorized email sending servers for your domain.
Why should I use SPF for my domain?
SPF helps confirm which mail servers are permitted to send emails on behalf of your domain, reducing the chances of email spoofing and increasing the trustworthiness of your emails with mail providers.
How does SPF affect email deliverability?
Properly configured SPF records can enhance email deliverability by ensuring that legitimate emails are accepted by inbox providers, reducing the likelihood of them being marked as spam.
What are some common SPF record configurations for major email providers?
For Gmail, include _spf.google.com in your SPF record, while for Microsoft, use spf.protection.outlook.com. These configurations allow the respective providers' mail servers to send emails on your behalf.
What happens if my SPF record exceeds 10 DNS lookups?
Exceeding the 10 DNS lookup limit can cause SPF validation to fail, potentially resulting in email delivery issues. It is important to consolidate your SPF records to avoid excessive DNS lookups.
How can I manage SPF records for multiple domains?
Each domain should have its own unique SPF record to track authorized senders accurately. Use tools and services that help minimize DNS lookups and manage records efficiently across multiple domains.
What are some common errors to avoid when creating SPF records?
Common errors include omitting the 'all' mechanism, using unsupported mechanisms, and exceeding DNS lookups. Always validate your SPF records to prevent configuration mistakes.
Does SPF protect against all forms of email spoofing?
No, SPF is only one part of a comprehensive email authentication strategy. Combining SPF with DKIM and DMARC offers more complete protection against email spoofing and related threats.
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"What is v=spf1 in an SPF record?","acceptedAnswer":{"@type":"Answer","text":"v=spf1 is the SPF record version identifier that indicates you are using the Sender Policy Framework to specify authorized email sending servers for your domain."}},{"@type":"Question","name":"Why should I use SPF for my domain?","acceptedAnswer":{"@type":"Answer","text":"SPF helps confirm which mail servers are permitted to send emails on behalf of your domain, reducing the chances of email spoofing and increasing the trustworthiness of your emails with mail providers."}},{"@type":"Question","name":"How does SPF affect email deliverability?","acceptedAnswer":{"@type":"Answer","text":"Properly configured SPF records can enhance email deliverability by ensuring that legitimate emails are accepted by inbox providers, reducing the likelihood of them being marked as spam."}},{"@type":"Question","name":"What are some common SPF record configurations for major email providers?","acceptedAnswer":{"@type":"Answer","text":"For Gmail, include _spf.google.com in your SPF record, while for Microsoft, use spf.protection.outlook.com. These configurations allow the respective providers' mail servers to send emails on your behalf."}},{"@type":"Question","name":"What happens if my SPF record exceeds 10 DNS lookups?","acceptedAnswer":{"@type":"Answer","text":"Exceeding the 10 DNS lookup limit can cause SPF validation to fail, potentially resulting in email delivery issues. It is important to consolidate your SPF records to avoid excessive DNS lookups."}},{"@type":"Question","name":"How can I manage SPF records for multiple domains?","acceptedAnswer":{"@type":"Answer","text":"Each domain should have its own unique SPF record to track authorized senders accurately. Use tools and services that help minimize DNS lookups and manage records efficiently across multiple domains."}},{"@type":"Question","name":"What are some common errors to avoid when creating SPF records?","acceptedAnswer":{"@type":"Answer","text":"Common errors include omitting the \"all\" mechanism, using unsupported mechanisms, and exceeding DNS lookups. Always validate your SPF records to prevent configuration mistakes."}},{"@type":"Question","name":"Does SPF protect against all forms of email spoofing?","acceptedAnswer":{"@type":"Answer","text":"No, SPF is only one part of a comprehensive email authentication strategy. Combining SPF with DKIM and DMARC offers more complete protection against email spoofing and related threats."}}]}